The nightmare scenario plays out with increasing frequency: your IT team discovers unauthorized access to customer data. Your phone starts ringing. Emails flood in. Social media erupts. In that moment, how you communicate can determine whether your business survives or becomes another cautionary tale.
Data breaches have become an unfortunate reality for organizations across every industry and size. From small healthcare practices to Fortune 500 companies, no one is immune. Cybercriminals are getting more sophisticated, and the consequences of a breach extend far beyond the immediate technical fix. What happens in the hours and days after discovery often determines the long-term damage to your reputation, customer relationships, and bottom line.
The financial toll can be staggering. Beyond potential regulatory fines and legal settlements, businesses face the hidden costs of customer churn, lost contracts, and diminished brand value. But there’s something even more insidious: the erosion of trust. Once customers question whether their data is safe with you, winning back that confidence becomes an uphill battle that can take years.
Here’s what many executives fail to grasp: managing a data breach goes far beyond IT concerns. It’s fundamentally a business crisis that requires strategic communications from the first moment.
The organizations that weather these storms successfully don’t just have better firewalls—they have clear communication strategies, decisive leadership, and often, experienced crisis communications professionals guiding them through the chaos.
Download Red Banyan’s free guide to Data Breach Communications.
Quick Links:
Why Data Breach Communications Matter
Step-by-Step Data Breach Communications Guide
Managing Social Media and Digital Channels During a Data Breach
Supporting Your Customers Through the Aftermath
Internal Communications: Keeping Your Team Aligned
Learning and Moving Forward: Turning Crisis into Opportunity
The Bottom Line: Communication Can Make or Break Your Data Breach Response
Frequently Asked Questions About Data Breach Communications
Why Data Breach Communications Matter
When a breach occurs, you’re not just dealing with compromised data. You’re managing multiple constituencies with competing needs and concerns. Your customers want to know if their information is safe. Your employees need clear direction on what to say and do. Board members demand answers about liability and financial exposure. Regulators may come knocking with compliance questions. The media might start calling for statements.
Each of these groups requires thoughtful, tailored communication. Generic statements won’t cut it. Silence is even worse. In today’s hyperconnected world, information vacuums get filled quickly—usually with speculation, rumors, and worst-case scenarios that may bear little resemblance to reality.
Your response becomes a referendum on your organization’s integrity. Customers are watching how you handle adversity. Are you transparent or evasive? Do you take responsibility or shift blame? Do you prioritize their security or your legal exposure? These judgments form quickly and stick around long after the technical aspects of the breach are resolved.
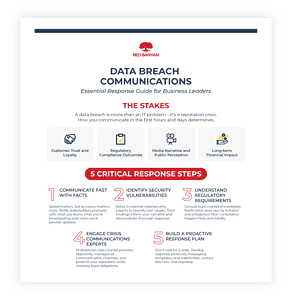
Step-by-Step Data Breach Communications Guide
Step 1: Move Fast with Factual Communication
Speed matters, but accuracy matters more. Your first communications set the tone for everything that follows. Rush out incomplete or inaccurate information, and you’ll spend weeks correcting the record. Wait too long, and speculation fills the void.
The key is getting the facts straight from the beginning. What exactly happened? When did it occur? What data was potentially compromised? What immediate actions have you taken? You might not have all the answers immediately, and that’s okay. What matters is being honest about what you know, what you don’t know yet, and when you’ll provide updates.
Different stakeholders need different levels of detail. Customers primarily want to know: Am I affected? What should I do right now to protect myself? Your internal team needs operational guidance. Regulators require specific compliance information. Craft your messages accordingly rather than taking a one-size-fits-all approach.
Timing your communications requires strategic thinking. While legal requirements often mandate notification within specific timeframes, smart organizations don’t wait until the deadline. Proactive communication demonstrates that you’re taking the situation seriously and putting customer interests first.
Step 2: Identify and Address Security Vulnerabilities
Understanding exactly what went wrong is critical—not just for fixing the immediate problem, but for communicating credibly about prevention. Customers and stakeholders need to hear that you’ve identified the root cause and taken steps to prevent recurrence.
This often means bringing in outside cybersecurity experts. Yes, it’s an additional expense during an already costly crisis. But having independent forensics specialists examine your systems accomplishes two important goals: they can identify vulnerabilities your internal team might miss, and their involvement signals to stakeholders that you’re taking a thorough, professional approach to understanding what happened.
As you work through the technical investigation, resist the urge to speculate publicly about causes or scope. Preliminary assessments often change as more information emerges. Stick with what you know for certain, and commit to transparency as you learn more.
Document everything. The investigation findings will inform not just your technical remediation but also your narrative about what happened and how you’re preventing future incidents. This documentation becomes crucial for regulatory compliance, insurance claims, and potential legal proceedings.
Step 3: Navigate the Regulatory Landscape
Data breach notification laws vary significantly by jurisdiction, and many organizations fall under multiple regulatory frameworks simultaneously. HIPAA for healthcare entities. State-specific breach notification laws. Industry-specific regulations. The complexity can be overwhelming when you’re already dealing with the crisis itself.
Getting this wrong has serious consequences. Failing to notify the right parties within required timeframes can trigger substantial fines and legal liability. Even if your breach notification complies with the letter of the law, poorly executed communications can still damage your reputation and customer relationships.
Work closely with legal counsel who understands both the regulatory requirements and the practical realities of crisis communications. The best lawyers recognize that while minimizing legal exposure is important, preserving business relationships and reputation requires a more expansive approach than simply meeting minimum disclosure requirements.
Notification isn’t just about compliance—it’s an opportunity to demonstrate responsibility. Organizations that go beyond minimum legal requirements, providing clear guidance and support resources to affected individuals, often emerge from breaches with their reputations more intact than those who take a purely legalistic approach.
Step 4: Partner with Crisis Communications Professionals
Your internal team knows your business, but they’re also deep in the crisis trenches. Emotions run high. Pressure builds. Fatigue sets in. Making clear-headed decisions about public communications becomes exponentially harder when you’re simultaneously managing the technical response, fielding stakeholder questions, and dealing with the stress of a major business crisis.
This is where experienced crisis communications professionals earn their keep. They’ve seen dozens or hundreds of similar situations. They know the pitfalls that seem obvious in hindsight but are easy to miss in the moment. They can objectively assess your situation and develop a strategic response that balances transparency, legal prudence, and reputational protection.
A skilled crisis PR firm brings several critical capabilities to the table. They craft messaging that’s clear, consistent, and calibrated to different audiences. They anticipate questions and develop thoughtful responses before you’re caught flat-footed. They coordinate across all your communication channels—press releases, website updates, social media, customer notifications, employee communications—ensuring everyone hears the same core message.
Perhaps most importantly, they serve as an objective third party who can tell you hard truths. When your legal team wants to say nothing and your CEO wants to say everything, experienced crisis counselors can navigate that tension and find the path that serves your long-term interests.
Red Banyan has extensive experience guiding organizations through data breach crises. Our team understands the unique challenges of healthcare data breaches, financial services incidents, and breaches affecting other regulated industries. We’ve helped clients navigate complex regulatory requirements while maintaining stakeholder confidence and protecting hard-earned reputations. You can see an example of our data breach crisis communications work in this HIPAA data breach case study.
Step 5: Build a Proactive Data Breach Response Plan
If you’re reading this article after a breach has occurred, you already know the value of preparation. The time to develop your response plan isn’t when the crisis hits—it’s beforehand, when you can think clearly and make deliberate choices.
A comprehensive data breach response plan addresses both technical and communications elements. Who needs to be notified immediately? What’s the decision-making chain of command? What are the trigger points for different levels of response? Who serves as the primary spokesperson? What pre-approved messaging templates can be quickly customized for the specific incident?
The plan should anticipate different breach scenarios. A ransomware attack requires different responses than an insider threat or a vendor compromise. Each scenario demands different messaging, different notification protocols, and different remediation steps.
Regular testing matters as much as the plan itself. Run tabletop exercises with key stakeholders. Practice your communication protocols. Update contact lists and notification procedures. Review and refine messaging templates. Like any emergency response capability, breach response skills atrophy without practice.
Building relationships with key partners before you need them pays dividends when crisis strikes. Identify potential cybersecurity forensics firms, legal counsel with data breach expertise, and crisis communications professionals. Having these relationships established means you can move quickly rather than starting from scratch when every minute counts.
The digital landscape has transformed how data breaches unfold. News spreads across social media within minutes. Customers take to Twitter or LinkedIn to voice concerns, ask questions, and share experiences. Employee speculation can leak out through personal social accounts. Competitors may even fan the flames.
Your social media strategy during a breach requires active management, not just monitoring. Set up dedicated monitoring to track mentions of your organization and the breach. Watch for misinformation that needs correcting. Identify legitimate customer concerns that need addressing.
Respond promptly and consistently. Have clear protocols for what your social team can say and when they need to escalate to leadership. Generic responses (\”We take security seriously and are investigating\”) may be necessary in the early hours, but they wear thin quickly. As your understanding develops, provide more substantive updates through official channels.
Your website should serve as the single source of truth. Create a dedicated page with breach information, FAQs, and regular updates. Point all other communications back to this central resource. This gives journalists, customers, and other stakeholders a reliable place to get accurate information rather than relying on secondhand accounts or speculation.
Notification is just the beginning of your customer communication journey. What happens next determines whether you keep their business and trust.
Provide concrete, actionable guidance. What specific steps should customers take right now? Should they change passwords? Monitor financial statements? Watch for phishing attempts? Be as specific as possible. Vague advice to \”remain vigilant\” doesn’t help anyone.
Consider offering tangible support services. Credit monitoring for financial data breaches. Identity theft insurance. A dedicated support hotline with staff who actually understand the situation and can answer questions. These gestures demonstrate that you’re not just checking legal boxes but genuinely concerned about customer welfare.
Keep customers informed as the situation evolves. When you complete your investigation, share the findings (appropriately). When you implement new security measures, explain what you’ve done. When you reach milestones in your recovery, update stakeholders. Ongoing communication shows you haven’t just moved on and forgotten about the incident.
Employees are both an audience and a channel. They need information to do their jobs effectively during the crisis, and they also serve as ambassadors who shape external perceptions through their own networks.
Brief your team early and often. They shouldn’t learn about the breach from news coverage or customer calls. Provide them with clear talking points so they can respond consistently when friends, family, or customers ask questions. Empower them with information rather than leaving them in the dark.
Acknowledge the stress your team is under. IT staff may be working around the clock. Customer service representatives are fielding difficult calls. Communications teams are managing an onslaught. Leadership visibility and support matter during these intense periods.
Create clear escalation paths. When employees encounter questions they can’t answer or situations they can’t handle, they need to know exactly where to turn. Confusion breeds inconsistency, and inconsistency undermines your message.
Every crisis contains lessons if you’re willing to extract them. Once the immediate fire is out, conduct a thorough post-mortem that examines both technical and communication elements of your response.
What worked well? What fell short? Where did communications break down? What questions kept coming up that you weren’t prepared to answer? What aspects of your plan proved unrealistic or incomplete?
Document these lessons and update your response plan accordingly. Share insights across your organization so different departments can learn from the experience. This institutional knowledge becomes invaluable if you face future incidents.
Consider how you can rebuild trust and emerge stronger. Some organizations have actually strengthened customer relationships by handling breaches exceptionally well. Transparency, swift action, and genuine care for customer impact can demonstrate character in ways that smooth sailing never could.
Technical remediation is necessary but not sufficient. How you communicate during and after a data breach often determines the ultimate impact on your organization.
The best outcomes come from organizations that prepare in advance, act decisively when breaches occur, communicate transparently with all stakeholders, and partner with experienced professionals who can guide them through the complexity.
Data breaches will continue to occur. The question isn’t whether your organization might face one, but whether you’ll be ready to manage it effectively when it happens. Your reputation, customer relationships, and business continuity depend on having both the plan and the communications expertise to navigate these turbulent waters.
If you’re facing a data breach or want to prepare your organization for potential incidents, Red Banyan’s crisis communications team can help. We’ve guided organizations through some of their darkest moments and helped them emerge with their reputations intact. Contact us or schedule a call with one of our crisis communications experts to learn how we can support your data breach preparedness and response efforts.
Frequently Asked Questions About Data Breach Communications
How quickly should we notify customers after discovering a data breach?
While legal requirements vary by jurisdiction and industry, most regulations require notification within 30-90 days of discovering a breach. However, waiting until the legal deadline can damage trust. Best practice is to notify affected individuals as soon as you have confirmed what data was compromised and can provide actionable guidance. Balance the need for speed with the need for accuracy—rushed notifications with incomplete or incorrect information create more problems than they solve.
What should we say if we don’t know the full extent of the breach yet?
Honesty is your best strategy. Acknowledge what you know for certain, be transparent about what you’re still investigating, and commit to providing updates as you learn more. A statement like, \”We discovered unauthorized access to our systems on [date]. We’re working with cybersecurity experts to determine the full scope and will provide updates within [timeframe]\” shows you’re taking action without overcommitting to information you don’t have yet. Include what immediate steps you’ve taken and what affected parties should do now.
Should we issue a press release about our data breach?
Whether you need to issue a press release is often determined by industry regulations and the type of information that was compromised. Before making any public announcements, consult with legal counsel to understand your disclosure obligations. Some industries and jurisdictions mandate specific notification procedures, including public disclosure requirements. Beyond legal mandates, factors like the breach’s scope, the sensitivity of compromised data, and your organization’s public profile all influence whether a press release is strategically advisable. Your lawyer can help you understand what you’re required to disclose, while a crisis communications professional can advise on how to communicate that information in a way that protects your reputation while meeting legal obligations.
How do we handle social media during a data breach crisis?
Social media requires active monitoring and rapid response during a breach. Set up keyword alerts for your brand name and related terms. Respond to customer questions with empathy and direct them to your official information source (typically a dedicated webpage with breach details and FAQs). Don’t delete negative comments unless they violate platform guidelines—this looks like you’re hiding problems. Have pre-approved holding statements ready for your social team to use while developing more detailed responses. The goal is showing you’re present, listening, and taking the situation seriously.
What’s the difference between a data breach and a cybersecurity incident?
A cybersecurity incident is any event that threatens the security of your information systems—attempted hacking, malware detection, system vulnerabilities, etc. A data breach is a specific type of incident where unauthorized parties actually access, steal, or expose sensitive data. Not every cybersecurity incident becomes a data breach. The distinction matters because breach notification laws typically only trigger when data is actually compromised, not just when an attack is attempted or detected. However, from a communications standpoint, you should still inform relevant stakeholders about serious security incidents even if no data was ultimately compromised.
Do we need to hire a crisis communications firm for every data breach?
The decision depends on several factors: the breach’s size and severity, your internal communications capabilities, regulatory complexity, and potential reputational impact. Small breaches affecting minimal data may be manageable with internal resources and legal counsel. However, breaches involving thousands of records, sensitive information (health, financial, personal), potential media attention, or complex regulatory requirements typically benefit from professional crisis communications support. Even if you have a strong internal PR team, they’re managing the crisis alongside you—outside expertise provides objectivity and specialized experience that’s hard to replicate internally.
What should our employee communications include during a data breach?
Internal communications should cover: what happened (facts you can share), what the company is doing to address it, how this might affect employees personally if employee data was compromised, what employees should say if customers or others ask them about it, and where to direct questions they can’t answer. Provide talking points, not scripts—employees need to sound authentic. Update your team before external announcements whenever possible so they don’t learn about the breach from news coverage. Regular updates maintain trust and prevent rumors from filling information gaps.
How long does it take for an organization’s reputation to recover from a data breach?
Recovery time varies dramatically based on how the breach is handled. Organizations that respond transparently, take responsibility, and demonstrate genuine concern for those affected can begin rebuilding trust within months. Those that minimize the issue, appear defensive, or fail to prevent recurrence may struggle for years. Research shows customers are often willing to give companies a second chance if they handle the crisis well—but ongoing communication, visible security improvements, and consistent follow-through are essential. The initial response matters, but the sustained effort to rebuild trust determines the ultimate timeline.
Should we apologize for a data breach?
Yes, with the right framing. Express genuine regret that the breach occurred and acknowledge the concern and inconvenience it causes. However, work with legal counsel on the specific language. You can say \”We deeply regret this incident occurred and apologize for any concern it has caused\” without making broad admissions of fault that could create legal liability. The tone should convey responsibility and empathy while being precise about what you’re apologizing for. What matters most is that your apology feels sincere and is backed by concrete actions to help those affected and prevent future incidents.
What role does the CEO play in data breach communications?
CEO involvement signals that leadership takes the breach seriously. For major incidents, the CEO should be visible in communications—whether through a video message, signed letter to customers, or media interviews. This demonstrates accountability and shows the issue has the highest level of attention. However, the CEO shouldn’t be the sole communicator. Different spokespeople serve different purposes: technical experts for detailed security questions, legal counsel for regulatory matters, customer service leaders for support issues. The CEO’s role is setting the tone, demonstrating leadership, and making clear the organization’s commitment to making things right.